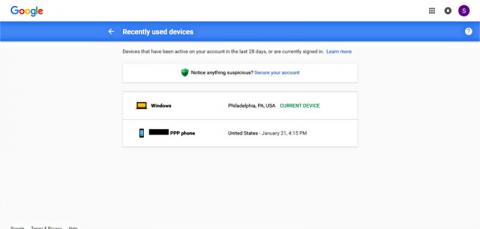
Urgent warning: Cops rooting through activist email accounts using stolen phones
https://twitter.com/georgejoseph94 is reporting evidence that police are using cell phones stolen from activists caught in the mass arrest at DisruptJ20 to log into email accounts of activists. Anyone with such an account needs to change their passphrase and lock out their former devices, and may want to close and replace the offending accounts RIGHT NOW if possible.
The attached photo is a screenshot of a Twitter account showing activity while the owner's phone was in police hands. Clearly the pigs are interested in more than just what was going on in the streets. The unprecedented threats, hacking, and infiltration efforts by the alt-right prior to the Inauguration combined with the equally unprecedented charges and investigative techniques suggest the Trump regime has adopted a strategy of using both law enforcement and "contractors" (Veritas got $10,000 from Trump) for a no-holds barred campaign against all dissent.
We now live in what is very close to an openly declared Fascist state, our security precautions must reflect this ugly reality. Even the cheapest Android phones support encryption, and can be encrypted with passphrases that are far more difficult to brute-force than the common "knock pattern" used for a simple screen lock.
Encrypting phones today won't get back the emails cops are now reading, but it may well prevent future rounds of emails and end to end encrypted text messages from being read. That can deny police information about legal strategies in the current round of felony cases, and deny them advance knowledge of protest plans entirely.
While most cell phone encryption can be broken (as we saw in the iPhone case) due to weak passphrases, it still takes hours per device. Multiply this by that box of 200+ phones the pigs are not rooting through and it becomes time impractical to crack them all. If 200 phones are encrypted with weak passphrases that take an average of an hour to crack, that's 200 hours, or 8 days of 24-7 password cracking. Use of strong passphrases that take a full day to crack would open this up to 200 days or 3/4 of a year of 24-7 work.